Forgot Password → Forgot Validation: a broken reset flow that enabled account takeover (researcher case study)
A defensive case study: a reported broken password-reset flow that allowed account takeover when tokens were not validated or bound to accounts. Read for detection, mitigation, and secure design - no exploit steps provided.
Disclaimer (mandatory): This article is educational and defensive. It summarizes a third-party researcher’s responsible disclosure about a broken password-reset flow. This write-up intentionally omits detailed exploitation instructions. Use the material to test and fix your own systems or in authorized engagements only.
TL;DR
A researcher discovered a password-reset implementation that issued reusable or unlinkable tokens and accepted token confirmation without correlating the token to a specific account or other context. Combined with user-enumeration signals, this allowed account takeover at scale. This post explains what went wrong, how defenders can detect it, robust architectural fixes, and test plans - without providing step-by-step exploit instructions.
1 - What the problem looked like (high-level)
In the reported case the application offered a standard "Forgot Password" flow. From the outside the flow looked normal:
- A user submits an identifier (email/username) to request a password reset.
- The system issues a reset token and sends a link containing that token.
- The link directs the user to a page where they supply a new password and the server validates the token and performs the reset.
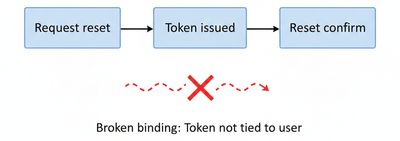
The design flaw was in step 3: the backend validated the reset token independent of the authenticated/target account or other binding context - in other words, the token was not cryptographically or operationally bound to the specific account that requested it. Additionally, two operational weaknesses amplified the impact:
- User enumeration: responses leaked whether an identifier existed, enabling an attacker to build a list of valid targets.
- Insufficient token lifecycle controls: tokens were long-lived, not single-use, or not tied to a client fingerprint or nonce.
Those weaknesses combined to enable account takeover: if an attacker obtained or guessed a valid token and the token could be applied against a different account, the attacker could reset passwords without owning the target’s inbox or authorization.
Key lesson: tokens are only useful when they are bound to the right resource and used in a single, tightly controlled transaction.
2 - Why this is more than "just a bug"
Broken reset flows are high-impact because they defeat authentication and authorization guarantees. Consequences include:
- Account takeover - direct compromise of user accounts, potentially including admin or privileged users.
- Privilege escalation - if the reset flow affects service accounts or staff logins.
- Chainable attacks - theft of API keys, personal data, or further lateral movement inside the system.
- Automated mass abuse - with enumeration and automation, the flaw can be scaled.
Because of this impact, such issues commonly receive high severity in bug bounties and incident triage.
3 - Where implementations commonly go wrong (anti-patterns)
Below are common anti-patterns that lead to these kinds of failures:
- Unbound tokens - tokens that are valid for any account or any operation instead of being cryptographically tied to a specific account ID and purpose.
- Token reusability - tokens that remain valid after first use.
- Lack of token entropy or weak encoding - easy to guess or derive tokens.
- Missing single-purpose typing - same token used for multiple flows (reset, invite, verify).
- Informative enumeration responses - different error messages or timing between “user not found” and “email sent”.
- Insufficient expiry or revocation - tokens valid for long windows and not revoked on suspicion.
- Missing contextual checks - no binding to originating IP range, device, or challenge when high risk is suspected.
4 - Detection and monitoring (how to find these problems safely)
If you’re defending an app, look for the following signals and add the checks below to monitoring and tests. These are defensive steps and intentionally do not include attack recipes.
Automated detection checklist
| Check | Why it matters |
|---|---|
| Check for identical token acceptance across different account IDs | Tokens should be valid only for the account that requested them |
| Test token single-use enforcement | Tokens must be invalidated after a successful reset |
| Monitor unusual token usage patterns | Repeated token submissions or same token used against different accounts are red flags |
| Observe differences in response bodies / timings for valid vs invalid identifiers | Distinct behaviour enables enumeration |
| Track token age and expiry distribution | Long lifetimes increase risk window |
Monitoring rules to implement
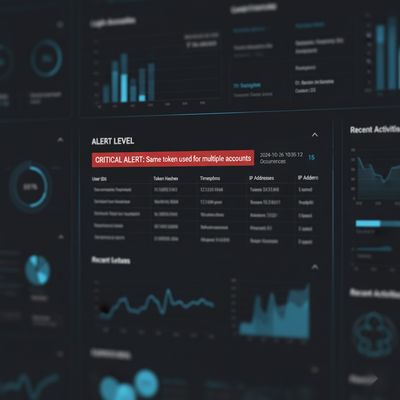
- Alert on: same reset token used for more than one account ID in a short interval.
- Alert on: many password reset requests for many different accounts from a single source IP or API key.
- Log the payloads and timestamps (do not log raw tokens in plaintext - log token hashes) and build grafof token → account mappings for forensic validation.
5 - Secure design principles (how to fix it)
Below are robust, industry-standard recommendations for secure reset flows. These are prescriptive and safe to implement.
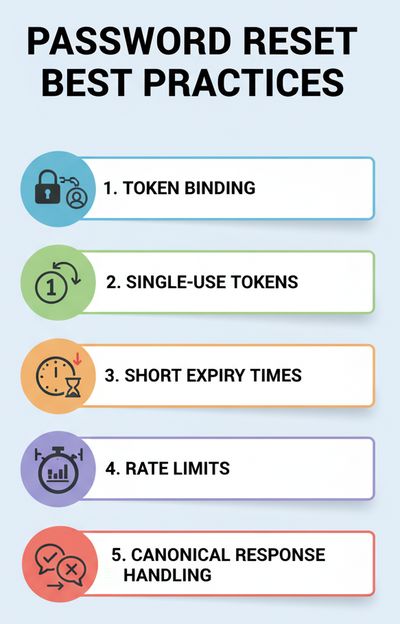
1) Bind tokens cryptographically and operationally
- Crypto binding: generate tokens that encode (or MAC) the account identifier and purpose (e.g.,
reset), so the server can verify the token includes the intendeduser_id. Use authenticated encryption or an HMAC over{user_id, purpose, expiry, nonce}rather than opaque sequential keys. - Operational binding: at issuance record the intended
user_id, the issuing IP, and a hash of token. Validate that the token presented maps exactly to the sameuser_id.
2) Single-use & immediate revocation
- Mark tokens as consumed once used and reject replay attempts.
- If a token is used or a reset is performed, revoke any outstanding tokens for that
user_id.
3) Short lifetime and claim limits
- Use short expirations (minutes to a few hours depending on risk profile).
- Limit the number of outstanding tokens per account (e.g., 1 or 2) and rotate.
4) Avoid user enumeration leaks
- Return the same generic response for "request sent" vs "request received for unknown user" (e.g., "
If an account exists, you will receive an email with next steps."). Use identical status codes and similar response bodies/timings. - Back this with silent logs (so admins can still triage) but don’t reveal existence to the caller.
5) Rate limit & anomaly detection
- Rate limit reset requests per IP, per account, and per API key.
- Add progressive throttling and CAPTCHA after suspicious activity.
6) Multi-channel verification for high-value flows
- For sensitive accounts (admin, finance), require an additional second factor or out-of-band confirmation (e.g., SMS code, authenticator) before accepting a reset.
7) Test harness & CI checks
- Add unit tests asserting token binding, single-use semantics, and no difference in API responses for valid vs invalid identifiers.
- Include fuzzing in staging for reset endpoints (only in controlled environments).
6 - Safe pseudocode patterns (defensive examples)
Below are defensive pseudocode snippets showing token issuance and validation patterns. These are safe examples: they show what to do, not how to exploit.
7 - Incident response & triage guidance
If you discover or are alerted to this weakness in production, follow these steps:
- Immediately revoke all active reset tokens (rotating secret keys if necessary).
- Force password resets for high-risk accounts (admins, finance).
- Rate-limit or temporarily disable public reset endpoint while investigating.
- Rotate any short-lived tokens or session cookies potentially exposed.
- Forensic log analysis: look for same-token usage across accounts and anomalous reset patterns.
- Communicate transparently to affected users: explain what happened, what was done, and recommended user actions (password change, 2FA enablement).
8 - Reporting & responsible disclosure (how researchers should proceed)
If you are a researcher who discovered such a flow, the responsible path is:
- Do not test at scale or execute account takeover on live user accounts.
- Capture minimal evidence (screenshots, non-sensitive logs) to demonstrate the problem.
- Provide clear reproduction steps at the level of "I can confirm the reset endpoint accepts tokens without binding to account X" - avoid sending or publishing tokens or direct exploit payloads.
- Report to the vendor following their security disclosure policy; if they lack a policy, report via the contact address with encrypted mail if available.
- If the vendor is unresponsive and user risk is high, consider coordinated disclosure via a recognized platform or CERT after following ethical guidelines.

9 - Realistic testing checklist for engineers (authorized environments only)
- Validate tokens across many accounts in staging only, ensuring mismatches are rejected.
- Add unit tests that attempt token replay and token cross-account application - assert failure.
- Build smoke tests that assert the reset API produces identical public responses for known and unknown identifiers.
- Simulate mass reset requests and ensure rate limits and CAPTCHA kick in.
10 - Closing thoughts
Authentication flows are one of the highest-value attack surfaces. Small mistakes in token design, lifecycle, or response messaging can create catastrophic failure modes. The case summarized here is a reminder that:
- Security is a system property - the safe behavior emerges from correct cryptography + correct operational controls + careful UX decisions that avoid leaking information.
- Test reset, invite, and verification flows as rigorously as you test login endpoints.
- Invest in logging, detection, and rapid revocation capability - those controls make the difference between a recoverable incident and a major breach.
References & further reading
- OWASP Authentication Cheat Sheet - reset flows & tokens
- NIST SP 800-63 (Digital Identity Guidelines) - lifecycle and verification
- "Designing Secure Password Reset" - various secure engineering blogs and RFCs