$500 OTP Bypass: The Duplicate That Taught a Bigger Lesson
A detailed breakdown of how a simple logic flaw in OTP verification led to full access without validation - and why duplicates still matter in bug bounty hunting.
Disclaimer: This post is for educational and defensive learning only.
It explores a real-world bug bounty finding reported by another security researcher.
The purpose is to help developers, testers, and learners understand how logic flaws in OTP verification can compromise authentication workflows - and how to prevent them.
🧩 Introduction: The Beauty of Broken Logic
Every bug bounty hunter dreams of that one alert - the validation email that says “Rewarded: $500.”
But behind every payout, there are countless duplicates, dead ends, and near-misses that shape the hunter’s instincts.
This story isn’t about the bounty. It’s about the lesson behind a duplicate, and how a researcher’s curiosity turned a routine OTP verification flow into a critical bypass discovery.
It’s the perfect case study of why authentication logic testing still matters - and how skipping a single validation check can expose an entire user flow.
🧪 The Setup: A Normal OTP Flow That Hid a Surprise
The target was a typical web application with a standard signup/login workflow.
New users had to verify their email addresses using a 6-digit One-Time Password (OTP) sent via email before accessing their dashboard.
On paper, this was a sound implementation:
- User registers an account.
- System sends an OTP to their email.
- User enters the OTP → verification successful.
- Access is granted to internal routes like
/dashboard,/settings, or/profile/edit.
The researcher followed this flow, completed verification, and began exploring the internal endpoints.
🧭 Endpoints of interest were:
/dashboard/settings/profile/edit
At this point, everything behaved normally. Verification worked, and access was granted post-OTP confirmation.
But the story doesn’t end there.
🔁 The Second Attempt: Curiosity Pays Off
Like any good security researcher, the hunter decided to test the process again, but this time with a twist.
They created a second account, not to bypass anything - but to verify consistency across new sessions and users.
The app once again sent a 6-digit OTP email.
However, instead of entering the code, the researcher had a thought:
“What if I just skip the OTP screen and try accessing a known internal path directly?”
They copied /profile/edit - a path they knew existed - and pasted it straight into the browser’s address bar.
Then they hit Enter.
💥 Access granted.
No OTP.
No validation.
No warning.
They were inside the new account’s internal panel - completely unverified.
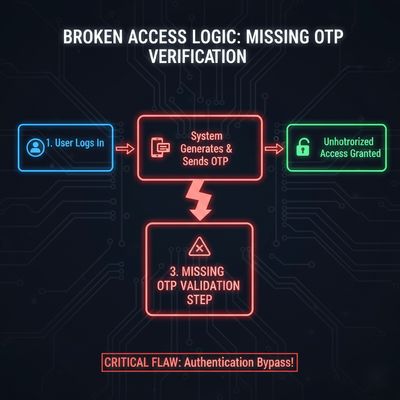
This was not a visual glitch or client-side trick. It was a full backend logic flaw that allowed users to bypass email/OTP verification entirely.

🧠 Why This Was Serious: A Logic Flaw with Real Impact
This wasn’t just a minor misconfiguration - it was a fundamental trust failure in the authentication layer.
🔓 What Happened Technically
The web application likely used session-based access control without enforcing verification status server-side.
When the user registered, the system probably:
- Created a user session immediately after registration.
- Flagged a “verified” status but didn’t validate it on every route.
- Failed to enforce OTP verification before granting access to protected pages.
In simpler terms:
The system created a door that was supposed to be locked - but forgot to check the key when someone walked in.
💣 The Potential Impact
Such a flaw could have serious implications:
- Automated account creation without email ownership.
- Spam accounts or bot registrations overwhelming the system.
- Bypass of 2FA/identity verification, allowing attackers to interact with core features.
- Data exposure or unauthorized access if combined with other insecure endpoints.
Even if it didn’t immediately grant administrative control, this bug undermined the trust boundary that email verification establishes - a critical piece of most modern signup systems.
📤 Reporting the Bug: The $500 That Got Away
The researcher crafted a clear, well-documented report including:
- Step-by-step reproduction instructions.
- Screenshots of the OTP flow and bypass.
- Technical analysis of potential backend validation issues.
- Recommended fixes for enforcing verification checks.
They submitted the report to the company’s bug bounty program, expecting a positive outcome.
Within a few days, the triager responded:
✅ “Valid issue.”
✅ “High impact confirmed.”
Then came the inevitable:
❗“Duplicate of a previously reported vulnerability.”
And with that, the payout - a $500 reward - slipped away.

💸 The “Almost” Payout: When Duplicates Teach the Best Lessons
Every bug hunter knows the bittersweet sting of duplicates.
You find the bug, prove the impact, and then… someone else beat you by a few days.
But duplicates are not failures - they’re validation.
They prove that your thought process, methodology, and instincts are spot on.
In this case, the researcher learned the right way to think:
- Always test authentication boundaries.
- Always revisit known paths after flow disruptions.
- Always assume that “client-side restrictions” can be bypassed.
This logic flaw was simple - yet devastating - and that’s what made it beautiful.
🕵️♂️ Step-by-Step Breakdown: How It Could Be Found (Ethically)
If you’re learning bug hunting, here’s a high-level safe guide to understanding and testing similar issues - responsibly.
-
Map Every Auth Flow
- Identify endpoints triggered during signup, login, and OTP verification.
- Record internal paths post-verification (e.g.,
/dashboard,/user/settings).
-
Use a Second Account
- Register a new user but don’t complete OTP verification.
- Observe which cookies or tokens are set before OTP success.
-
Replay Known Paths
- Try accessing known authenticated routes directly from the unverified account.
- Watch server responses - 200 means accessible, 401/403 means blocked correctly.
-
Analyze Server Logic
- Check whether the backend checks for verification flags (
is_verified == true). - If not, you’ve found a broken access control flaw.
- Check whether the backend checks for verification flags (
-
Document Everything
- Use screenshots, session details, and clear explanations.
- Always report ethically - never exploit real user data.
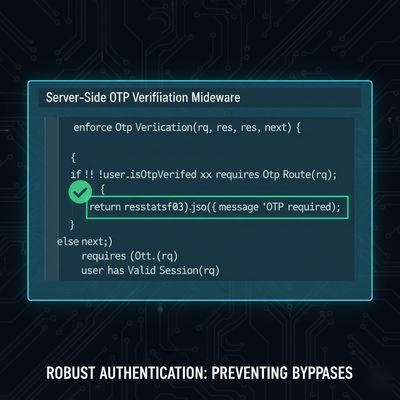
🧰 Developer’s Defensive Perspective
Developers can easily prevent such issues with proper server-side validation and middleware logic.
Here’s how:
Key Best Practices:
- Enforce verification flags server-side on all protected endpoints.
- Avoid granting session tokens before verification success.
- Apply rate-limiting and anti-automation for registration and OTP endpoints.
- Log and monitor unusual access to “restricted” routes.
- Use API middleware to standardize authorization checks.
🧭 Lessons for Hunters & Developers
For Bug Hunters:
- Always test multi-step flows twice - before and after critical checkpoints.
- Don’t ignore simple ideas - skipping one step can reveal deep logic flaws.
- Duplicates are milestones, not mistakes. They show you’re thinking like the best.
- Focus on reliability and reproducibility in reports - that’s how you earn respect.
For Developers:
- Treat every verification process as a security boundary.
- Centralize your access control logic - don’t rely on client indicators.
- Audit every “post-registration” route to confirm verification enforcement.
💬 Final Thoughts
This $500 OTP bypass wasn’t about the bounty - it was about perspective.
Security isn’t just about clever payloads or high-tech exploits.
Sometimes, it’s about noticing what’s missing - a simple check, a missing flag, a forgotten gate.
The researcher didn’t win money that day, but they walked away with something far more valuable:
A deeper understanding of how logic flaws are born - and how to spot them early.
So next time you hit a duplicate, don’t get discouraged.
Celebrate it. It means you’re thinking like a pro.
Because every “almost bounty” is just one bug closer to your breakthrough.

References
- OWASP Authentication Cheat Sheet
- PortSwigger: Logic Flaws in Authentication
- HackerOne Reports: OTP and Email Verification Bypasses
- Bugcrowd University: Authentication and Authorization Testing
Published on herish.me - helping the next generation of ethical hackers learn from real-world vulnerabilities.