Critical Auth Bypass in Government App via Hardcoded OTP Logic
A severe authentication flaw in a government mobile app allowed login using hardcoded OTP values.
Disclaimer
This article is published for educational and defensive cybersecurity awareness.
All testing was performed legally under responsible disclosure guidelines.
The name of the government app is intentionally withheld to avoid misuse.
Introduction
Authentication systems are the foundation of digital security - especially in public-sector mobile apps handling sensitive user data, departmental workflows, or government communications. Even a small mistake in login logic can expose an entire system to unauthorized access.
In this case study, a security researcher analyzing an Indian government-issued Android mobile application encountered a critical authentication bypass. The flaw allowed anyone to log in using a hardcoded mobile number and static OTP, effectively skipping all real verification steps.
Although the vulnerability has been fixed following responsible disclosure to CERT-In, the incident highlights how fragile authentication mechanisms can become when proper server-side validation is missing.
This blog provides a full breakdown of the issue, safe reproduction steps (in a lab environment), the root cause, real-world impact, and actionable defenses for mobile developers and security teams.
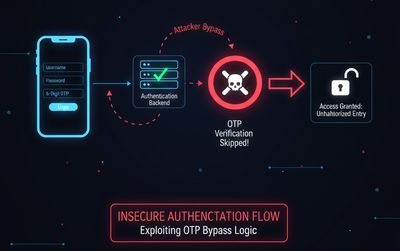
Understanding the App's Authentication Flow
Government mobile apps typically rely on OTP-based authentication for user verification. The general workflow is:
- User provides a mobile number.
- Server sends a One-Time Password (OTP).
- User enters OTP.
- Server validates the OTP.
- Access is granted.
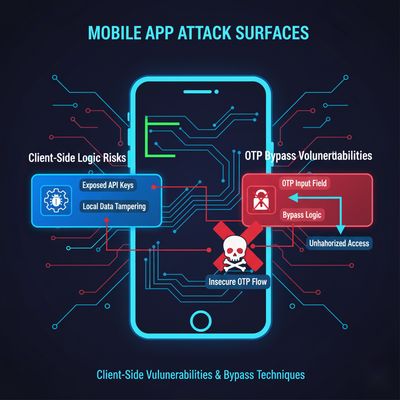
In this case, however, the application mistakenly trusted client-side values rather than server-side validation. This trust was the root of the authentication bypass.
What Was Expected
- The server should validate the mobile number.
- An OTP should be generated uniquely per session.
- The OTP should be validated securely server-side.
What Actually Happened
- A single hardcoded mobile number (“0000000000”) was treated as valid.
- A static OTP (“123456”) always passed authentication.
- No server-side verification occurred.
- The mobile app simply accepted these values and unlocked full features.
This turned an intended verification mechanism into a complete bypass.
Step 1 - Recon & Discovery
The researcher began analyzing the app behavior to understand the underlying authentication flow. Observations included:
- OTP requests were sent to an endpoint but no actual SMS was generated.
- The app allowed users to continue even if the device wasn’t registered.
- Entering arbitrary mobile numbers resulted in error responses.
- But entering a specific hardcoded mobile number behaved differently.
The researcher then tested common patterns used in poorly designed authentication systems, such as:
- Reusing known admin/test numbers
- Entering placeholder strings
- Trying common hardcoded test OTPs
This process led to the discovery of the bypass.
Beginner Breakout: Why Hardcoded Credentials Are Dangerous
Hardcoded credentials often exist because developers use them in testing environments. If not removed before production:
- Anyone discovering them gains full access
- They bypass all authentication controls
- They undermine the entire security model
This vulnerability fits CWE-798: Use of Hard-coded Credentials.
Step 2 - Understanding the Vulnerability
The authentication flow behaved as if the OTP validation step was entirely optional. Instead of forwarding OTP input to a server, the application:
- Accepted the OTP directly on the client
- Matched it against a hardcoded value
- Granted access regardless of user identity
This corresponds to:
- CWE-287: Improper Authentication
- OWASP A01:2021 - Broken Access Control
Why It Happened
Based on the observed behavior, the likely causes include:
-
Local OTP Verification
Instead of validating the OTP server-side, the app contained hardcoded logic. -
Debug/Test Logic Left in Production
Developers sometimes add shortcuts for internal testing:- Hardcoded test mobile numbers
- Static OTP values
- Debug bypasses
These must be removed before deployment.
-
Absence of Server-Side Enforcement
Authentication decisions were made entirely on the client - meaning attackers could easily spoof the flow.
Beginner Breakout: Client-Side Logic Cannot Be Trusted
Anything running on a user’s device can be:
- Modified
- Reverse-engineered
- Bypassed
- Tampered with
Strong authentication must always be validated by the server, not the app.
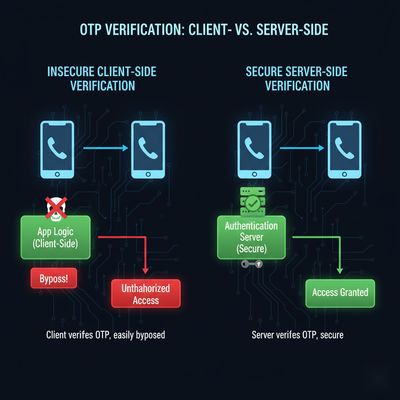
Step 3 - Building the Exploit (Safe, High-Level)
The following reproduction occurred in a secure lab environment and is provided purely for awareness.
Reproduction Steps (As Discovered by the Researcher)
- Install the government app (latest version).
- Select “Login Type”.
- Enter the mobile number:
0000000000 - Tap “Login with OTP”.
- Enter OTP:
123456 - Access is granted instantly - no SMS needed, no real verification.
This demonstrates a full authentication bypass using a test mobile number and static OTP.
Why This Works
Because the app:
- Did not validate the OTP with a backend server
- Trusted a static OTP value
- Allowed a test account to bypass all restrictions
This meant any user - even with no relation to the department - could log in.
Step 4 - Executing & Confirming the Exploit
Once logged in, the researcher confirmed:
- Access to restricted governmental functionality
- Ability to view internal dashboards or menus
- Exposure of non-public workflows intended for department personnel
- Potential access to data the user was not authorized to view
Even if the affected module didn’t expose sensitive data directly, authentication bypass alone creates severe systemic risk, allowing:
- Unauthorized access
- Privilege escalation
- Identity spoofing
- Misuse of departmental interfaces
The vulnerability’s severity was immediately clear.
Defensive Perspective
To prevent similar issues, mobile application developers and security teams must employ strong server-side authentication mechanisms.
Application-Level Mitigations
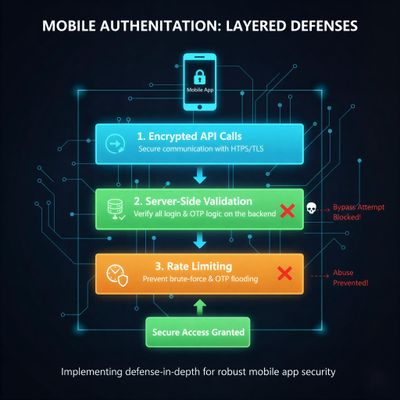
1. Enforce Server-Side OTP Validation
Every OTP must be:
- Generated server-side
- Bound to a session or request
- Validated server-side
The client should never be trusted with authentication decisions.
2. Remove Hardcoded Test Credentials
Ensure no logic such as:
- Backdoor OTPs
- Test mobile numbers
- Debug flags
- Local authentication shortcuts
exists in production code.
Perform secure code review before release.
3. Implement Rate Limiting
Protect OTP endpoints from brute force attempts and abuse.
4. Use Signed & Encrypted API Calls
Ensure integrity of requests by using:
- HMAC signatures
- HTTPS/TLS pinning
- Replay protections
Infrastructure-Level Mitigations
1. Require Mandatory Backend Verification
Even if the client indicates a successful OTP, the server must verify:
- Account validity
- OTP correctness
- Session integrity
2. Logging & Alerting
Enable logs for authentication attempts to detect:
- Repeated login bypass attempts
- Unusual mobile numbers
- Device irregularities
3. Secure Mobile CI/CD Pipeline
Use automated checks to scan builds for:
- Hardcoded credentials
- Debug code
- Sensitive strings
Real-World Impact
Authentication bypasses in government environments can have significant implications:
| Impact | Description |
|---|---|
| Unauthorized Access | Non-department users can access internal modules |
| Data Exposure | Potential leakage of sensitive internal information |
| Impersonation | Attackers can act as legitimate officials |
| Operational Interference | Misuse of workflow features |
| Regulatory Risk | Violations of privacy and compliance standards |
Even though the data accessed in this specific case was limited, the systemic risk was extremely high.
Troubleshooting & Pitfalls
1. OTP Arrives, But App Still Logs In Without It
This indicates client-side validation.
Always ensure OTPs are enforced server-side.
2. Hardcoded Credentials Found During Pentest
Treat this as a critical severity issue - not a low-risk bug.
3. Login Bypasses Only Work on Certain App Versions
This often happens when:
- A test build gets deployed accidentally
- Debug logic remains in production
- Two app branches merge incorrectly
4. Reverse Engineering May Reveal Hidden Flows
Mobile apps should assume adversaries can inspect:
- APK contents
- API traffic
- Authentication logic
Final Thoughts
This vulnerability underscores a vital truth: authentication must never live on the client.
Mobile apps that trust user input without server-side validation expose themselves to complete compromise, especially when paired with hardcoded test credentials or static OTPs.
The researcher responsibly reported the issue through the CERT-In disclosure program, and the organization swiftly patched it.
For developers handling sensitive or governmental applications:
- Always perform secure code reviews
- Remove test logic before deployment
- Validate every authentication step server-side
- Implement strict backend checks
Strong authentication is the front door of any secure system - and leaving that door unlocked can create risks far greater than intended.
References
- CWE-287: Improper Authentication
- CWE-798: Hardcoded Credentials
- OWASP Mobile Top 10
- CERT-In Responsible Disclosure Guidelines
- OAuth & OTP security documentation