Identity Hijacking via Faulty Email Schema Validation: A Deep Dive into a Business Logic Flaw
A critical business logic flaw allowed attackers to impersonate users by abusing email schema validation in a change-email workflow.
Disclaimer (Educational Purpose Only)
This article is written strictly for cybersecurity education.
All names, domains, and identifiable details are anonymized.
Only ethical testing, authorized research, and responsible disclosure are endorsed.
Introduction
Business logic vulnerabilities rarely get the same attention as technical exploits, yet their impact can be devastating. They bypass security not by breaking encryption or hijacking sessions, but by exploiting flawed assumptions in how an application thinks.
This article analyzes a subtle identity takeover technique discovered by security researcher Mahmoud Kroush, involving an online presentation-building platform (referred to as Redicted.com) where the email-change workflow was implemented incorrectly. The result? Attackers could impersonate any user without touching their password, without bypassing OTP, and without launching brute-force attacks.
The vulnerability stemmed from a misinterpretation of the email field - a tiny oversight in schema validation that cascaded into a complete identity takeover scenario.
This write-up breaks down the entire chain: how the flaw appeared, why it was so dangerous, and what developers and security teams can learn from it.
Understanding the Lab Setup
Redicted.com is a collaborative presentation platform where:
- Users create content
- Teams collaborate
- Email identity is central to trust and visibility
- Invitations and activities appear tied directly to a user’s email
This means the email field is not just a contact method - it is a user identity anchor.
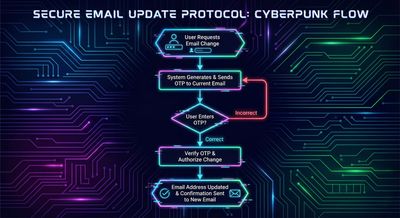
The Email Change Workflow
The application’s legitimate workflow was intended to look like this:
- User enters a new email
- User confirms new email
- User provides current password for verification
- System sends an OTP to the new email
- User enters OTP
- Email is updated
This is standard practice.
But the system treated the email field incorrectly - as something flexible and loosely validated, rather than as an immutable identity attribute. This opened the door for manipulation.
Step 1 – Recon & Finding the Weakness
The investigation began with examining authentication features. The core interest was the email-change flow, where identity verification depends entirely on where the OTP is delivered.
The first hint of trouble appeared when the server accepted unexpected datatypes in the email parameter. Instead of rejecting malformed values outright, the backend attempted to process them.
This surfaced the first anomaly.
When sending:
…the server accepted the array, processed it, and sent back a 200 OK response.
That single clue unraveled the deeper flaw.
Step 2 – Understanding the Vulnerability
Deep Dive
The backend accepted arrays and treated them as strings. When the application attempted to send a verification code, the array string was not recognized as a valid email. Instead of throwing an error, the server fell back to the previous valid email stored in the database.
This behavior led to several consequences:
- Attackers could submit invalid-looking emails that technically passed validation
- The platform failed to detect malformed input
- The system relied on the last known valid email for OTP delivery
- Identity confirmation steps could be misdirected or hijacked
The root cause was a schema validation failure.
Instead of:
…it behaved like:
Small bug. Big consequences.
Beginner Breakout: Why Is This Deadly?
Identity flows assume:
- Email = the person
- Email verification = the safeguard
- OTP = the gatekeeper
If an attacker can force the system to send the OTP to their own email, while appearing to request a change to the victim’s email, identity takeover becomes trivial.

Step 3 – Building the Exploit
1. Testing Arrays in Email Parameter
The researcher tested variations:
The server responded:
Then - crucially - sent the OTP to a completely different address, not the ones provided.
That exposed the logic flaw.
2. Observing Fallback Behavior
Further tests showed:
- Arrays, malformed strings, or invalid formats
- All caused the backend to revert to the last known valid email
This allowed an attacker to manipulate flow by predicting where the OTP would land.
3. Constructing Identity-Takeover Scenario
The exploit relied on three emails:
- Current Email - legitimate user
- Attacker Email - attacker controls
- Victim Email - a target the attacker wants to impersonate
Flow:
- User changes email from current → attacker.
- The OTP arrives at attacker_email; attacker confirms.
- Attacker attempts to change from attacker_email → victim_email.
- Server blocks - victim_email is already taken.
- Attacker appends a non-breaking space Unicode character:
- Backend accepts it as “new email”
- Backend attempts sending OTP to this modified email
- Modified email is invalid → backend reverts
- OTP is sent again to attacker_email
- Attacker confirms the OTP
- System treats attacker as victim
This bypasses:
- Ownership checks
- Identity validation
- Email uniqueness enforcements
- Email schema validation
- OTP protection
A single Unicode space changed everything.
Example Payload
Why \u00A0 Works
The non-breaking space:
- Is invisible in UI
- Is different in binary representation
- Survives server-side cleanup
- Tricks uniqueness validation
- Tricks display logic
- Breaks the email-sending subsystem
It’s a classic Unicode-based business logic exploit.

Step 4 – Executing & Confirming the Exploit
Once the attacker confirms the OTP (sent to attacker_email), the system updates the account to:
- Email displayed as victim_email
- Identity shown as the victim
- Invitations sent appear “from the victim”
- Activity logs show victim
- Profile name & picture can match victim
- All team interactions now impersonate the victim
Because the database now stores:
- victim@gmail.com
- victim@gmail.com + invisible space
…the UI and other services can no longer distinguish them.
This is a complete identity takeover.
Real-World Impact
The vulnerability enables:
- Impersonation
- Social engineering using the victim's identity
- Abuse of collaboration features
- Damage to trust, reputation, and workflow
- Sensitive information exposure
This is not hypothetical - it came directly from flawed data validation.

Defensive Perspective
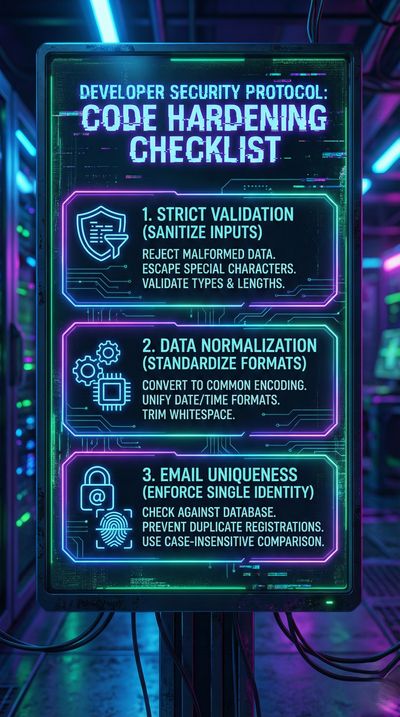
1. Strict Schema Validation
Email fields must follow:
- Explicit string type
- RegExp-validated format
- Prohibited characters (Unicode whitespace)
- Length limits
- No arrays, objects, or malformed structures
2. Enforce Strong Uniqueness
Comparisons should run on:
- Normalized email
- Trimmed email
- Lowercased email
- Canonicalized Unicode
Failing to normalize allows duplicate identities.
3. Reject Non-Scalar Inputs Immediately
Email arrays, null bytes, or malformed values should not reach business logic.
4. OTP Must Be Bound to New Email
OTP delivery should never fall back silently.
If email is invalid → reject request, don’t re-route.
5. Verify Token Target
Email tokens must store:
- Target email
- Expiration
- Pre-update state
- One-time-use constraints
6. Logging & Monitoring
Flag requests that:
- Include Unicode
- Include arrays
- Modify identity fields
- Trigger fallback behavior
Troubleshooting & Pitfalls
❌ Pitfall: Assuming “Flexible Input” Is Friendly
Developers often allow flexible input formats for convenience.
Attackers weaponize them.
❌ Pitfall: Trusting Client-Side Validation
Client can be bypassed instantly.
❌ Pitfall: Ignoring Unicode Threat Models
Unicode is a top-tier attack tool in identity workflows.
❌ Pitfall: Overrelying on OTP
OTP is only as strong as the address it is sent to.
❌ Pitfall: Misinterpreting “Low Technical Complexity”
This vulnerability is high-impact despite low complexity.
Final Thoughts
This case demonstrates how business logic flaws aren’t always obvious. The vulnerability didn’t require sophisticated payloads, advanced exploitation, or breaking cryptography. It came from understanding assumptions in workflow design and spotting inconsistencies.
Identity is fragile.
A single Unicode space, misprocessed by a backend, can flip it upside-down.
By studying these failures, developers and security professionals can strengthen the mechanisms that define user identity - the most important trust anchor in any online platform.

References
- Responsible disclosure conversation (private HackerOne program)
- Research insights by Mahmoud Kroush
- OWASP Input Validation and Business Logic guidelines