Reflected XSS to Account Takeover: A Deep Dive Into a Real-World Attack Chain
A detailed analysis of a reflected XSS flaw in a news platform that enabled session theft and account takeover across multiple regional programs.
Disclaimer
This article is for educational and defensive cybersecurity purposes only. No malicious activity was performed. All payloads, tools, and demonstrations were done in safe, controlled, and responsible environments. Never test real systems without explicit authorization.
Introduction
Reflected Cross-Site Scripting (XSS) continues to appear in production applications around the world. Even mature platforms with solid user interfaces can unintentionally expose dangerous injection points when older or unmaintained components are left running.
In this blog, I break down a real-world reflected XSS found by a security researcher in a widely used news platform. The vulnerability allowed session theft, full account takeover, and phishing-grade exploitation across six separate regional programs belonging to the same organization.
Although the payload and pop-ups shown in this case may appear simple, the underlying impact was significant. A single reflected XSS, combined with an external logging service and parameter discovery tools, turned into a dangerous attack chain.
This deep-dive will walk you through the researcher’s methodology, the technical flow, and the defensive measures every organization must adopt.
Understanding the Target Surface
The researcher started with broad reconnaissance to identify all assets within the scope of the organization. Instead of manually guessing subdomains, they used an online subdomain enumeration service:
- Identified all hosted platforms
- Grouped them by country
- Focused on older assets using outdated stacks
- Examined parameter-rich pages such as search, archive, and filtering interfaces
One of the regional news portals loaded older scripts and legacy services - a perfect spot for XSS testing.
Step 1 - Reconnaissance & Subdomain Enumeration
Before any payload testing, the researcher needed visibility into the application ecosystem. They used a public subdomain discovery tool to enumerate the organization's assets.
Tool used
subdomainfinder.c99.nl
This provided a wide list of subdomains like:
archive.example-country.comsearch.example-country.comedition.example-country.comlegacy.example-country.com
These older sites often contain outdated input validation routines - making them ideal for injection testing.
Recon tips for beginners:
- Always enumerate all subdomains
- Focus on outdated technologies
- Identify search and parameter-driven pages
- Map request/response patterns using a proxy
- Test quietly and safely without generating noise
Recon is often the difference between finding nothing and discovering impactful flaws.
Step 2 - Finding the Injection Point
The researcher focused on the search functionality of one regional platform. Search bars are classic XSS targets because:
- They echo user input back onto the page
- They rely on dynamic query parameters
- Validation is often inconsistent
- They are frequently overlooked by developers
After testing multiple payloads across different parameter variations, one eventually triggered a JavaScript execution.
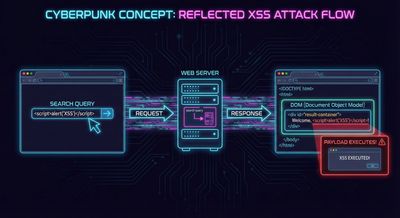
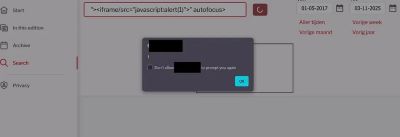
The working payload was:
This simple payload caused a reflected XSS pop-up - confirming the vulnerability.
Why this payload worked
The input was:
- Injected into the DOM without sanitation
- Rendered inside an attribute
- Parsed incorrectly due to unclosed quotes
- Executed automatically because of
autofocus
This gave the researcher a stable, reliable XSS on one of the company's active domains.
Step 3 - Validating the XSS (Safe & Controlled)
The researcher didn’t escalate without validation. They:
- Confirmed the payload worked consistently
- Tested multiple devices/browsers
- Verified execution only affected their account
- Avoided stealing real user data
- Ensured no sensitive information was exposed
A safe validation process is essential for responsible disclosure.
Beginners often rush to exploit impact without validating the context - avoid that mistake.
Step 4 - Expanding the Attack Surface With ParamSpider
Reflected XSS can be trivial or devastating depending on reachability.
To expand the injection vectors, the researcher used:
ParamSpider
A tool that scrapes URLs and extracts potential GET parameters from:
- WaybackMachine
- sitemap.xml
- robots.txt
- Hyperlinks
- Archived request logs
This tool allowed the researcher to discover additional parameters across the site:
?query=?content=?search=?filter=?redirect=
Each parameter became a potential injection point for XSS payloads.
With more vectors discovered, the researcher now had paths for phishing, redirection, and eventual session hijacking setups.
Step 5 - Escalating Impact Using an External XSS Logging Service
Reflected XSS alone isn’t always impactful unless chained with a second-stage action. To escalate the impact, the researcher leveraged:
xss.report (a legitimate XSS testing/logging service)
The platform generates payloads that, when executed, capture:
- Victim’s IP
- User-agent
- Cookies/session info (if accessible)
- Browser metadata
- Referrer details
- Any custom logged variables
The dashboard then displays this information in real time.
Example usage
The service provides polyglot payloads that can be inserted into vulnerable parameters.
When the victim loads the link:
- The payload executes
- Information is logged
- Researcher receives details in the dashboard
This is how session hijacking becomes possible - but only if the platform lacks cookie flags like HttpOnly, Secure, or proper session regeneration.
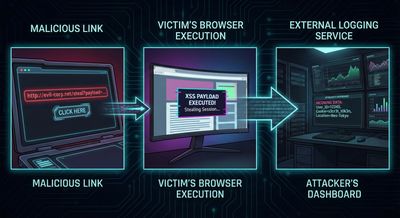
Step 6 - Weaponizing the Payload (Ethically and Safely)
Armed with ParamSpider’s discovered parameters and xss.report’s dynamic payloads, the researcher generated a harmless proof-of-concept link.
This link:
- Contained an encoded XSS payload
- Automatically executed when visited
- Logged the session information into the researcher’s dashboard
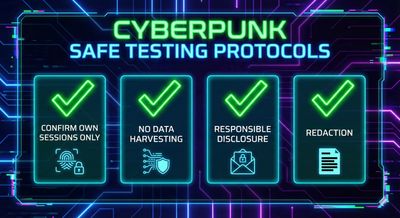
By responsibly testing with their own sessions only, the researcher confirmed:
- Session tokens were not protected using
HttpOnly - Cookies were accessible via JavaScript
- Account takeover was theoretically possible
This formed the basis of the responsible disclosure report.
Step 7 - Impact Overview
The XSS vulnerability existed across six country-specific news domains belonging to the same company. This significantly increased the severity because:
- Each domain had millions of monthly visitors
- Many users stayed logged in for personalized news
- The same vulnerability pattern repeated across multiple properties
- A malicious attacker could automate exploitation across all portals
Potential impact
| Impact | Description |
|---|---|
| Account Takeover | If sessions were accessible, attackers could fully access user accounts |
| Cookie Theft | Missing HttpOnly allowed JavaScript to read session cookies |
| Phishing Weaponization | Injected payloads could redirect users to credential-harvesting pages |
| Privacy Exposure | Victim metadata logged in external services |
| Mass Exploitation | Six programs were affected due to code reuse |
This impact demonstrates how a simple XSS becomes high severity when:
- Located on a high-traffic site
- Combined with session misconfigurations
- Exploitable across multiple domains

Step 8 - Responsible Disclosure
The researcher followed the proper responsible disclosure flow:
- Documented payload behavior
- Recorded responses
- Captured the affected endpoints
- Submitted reports to each regional bug bounty program
- Avoided real exploitation
- Tested only their own session tokens
- Avoided harvesting real user data
- Presented mitigation steps
Six reports were marked as duplicates because the issue affected each regional variant, but the researcher still fulfilled the ethical expectation of reporting everything.
Understanding Why Reflected XSS Still Happens Today
Despite being one of the oldest web vulnerabilities, reflected XSS remains common because of:
- Legacy codebases still in production
- Unmaintained templates and outdated frameworks
- Direct DOM injection without sanitization
- Query parameters being echoed without encoding
- Lack of modern security headers
- Development teams assuming search inputs are safe
- Improper testing for edge-case payloads
Organizations must treat even minor UI fields as potential injection surfaces.
Defensive Perspective
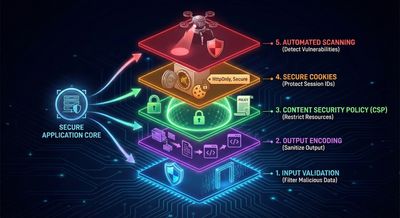
To protect against reflected XSS and prevent similar account takeover risks, organizations must adopt a layered security model.
Required Fixes
- Output Encoding
Use proper HTML-encoding (<,>,") before reflecting user input. - Input Validation
Reject suspicious characters like<,",',>when not required. - Content Security Policy (CSP)
Deploy strict CSP rules to prevent inline scripts:
script-src 'self'- Avoid using
unsafe-inline - Lock down third-party domains
- HttpOnly & Secure Cookies
Mark authentication cookies as:
HttpOnly→ prevents JavaScript accessSecure→ requires HTTPSSameSite→ prevents CSRF
- Escaping inside Attributes
Use proper attribute escaping when injecting values into HTML attributes. - Automated XSS scanning
Run tools like:
- Burp Suite’s Active Scanner
- ZAP’s XSS scanning module
- Nuclei templates
- GitHub CodeQL
- Legacy code audits
Audit all frames, templates, and old rendering engines.
Troubleshooting & Pitfalls
Many developers assume:
- “It’s just a search bar - harmless.”
- “Nobody will guess this parameter.”
- “JavaScript URLs never execute.”
- “We sanitized input in one location - we’re safe.”
But reflected XSS often appears:
- In error messages
- In templated HTML emails
- In outdated UI sections
- In untested alternative parameters
- In archived or regional versions
Security teams must test entire ecosystems - not just primary URLs.
Final Thoughts
This case highlights how a simple reflected XSS can escalate into a severe security risk when combined with:
- Poor cookie security
- Reused code across multiple regions
- Dynamic payload generation services
- Weak CSP policies
- Legacy search pages
Modern attackers do not rely solely on advanced exploitation. They use chaining - combining small cracks to form a large breach. This is why even “simple XSS” is powerful when applied in the right context.
Reflected XSS remains one of the most common - and most dangerous - vulnerabilities in the real world. Organizations must invest in:
- Strong validation
- Solid output encoding
- Secure cookie flags
- Proper content security policies
Ultimately, this finding reinforces an important reminder:
Never underestimate the impact of reflected XSS.
Stay safe, stay ethical, and always disclose responsibly.