Information Disclosure in Revive Adserver v6.0.0 via Verbose Errors
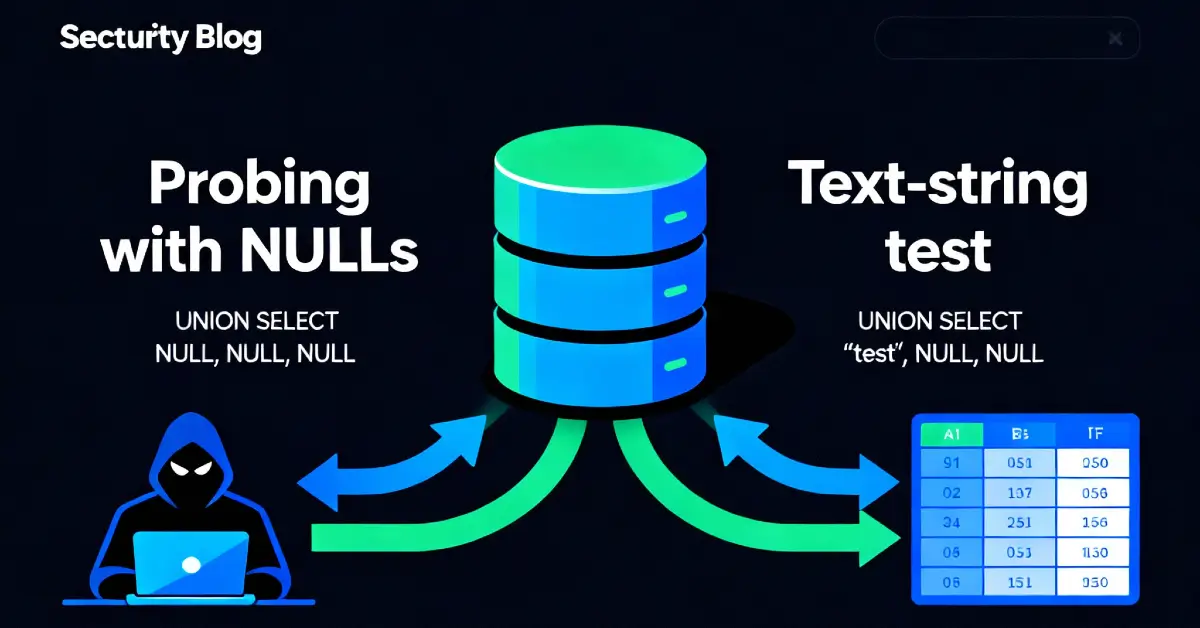
A detailed breakdown of an information disclosure vulnerability in Revive Adserver v6.0.0 where verbose error messages exposed SQL queries, database versions, and PHP environment details.
Read More